As cloud services have grown in popularity, they have also become a fertile ground for cybercriminals to launch attacks that stay under the radar. Attackers are taking advantage of the trust that users, organizations, and security vendors place in popular cloud services. This blog post provides examples of four key ways in which attackers abuse cloud services, for:
- Malware delivery
- Phishing
- Command and Control
- Malware propagation
This blog serves as a cautionary tale, highlighting why cloud services should be approached with a Zero Trust strategy.
You can read more articles from Netskope Threat Labs on their blog.
Malware delivery
The popularity of cloud apps for malware delivery is steadily increasing. Cloud-delivered malware now outnumbers malware delivered via the traditional web. Over the course of the past year, cloud-delivered malware grew from 48% to 61% compared to traditional web delivery.
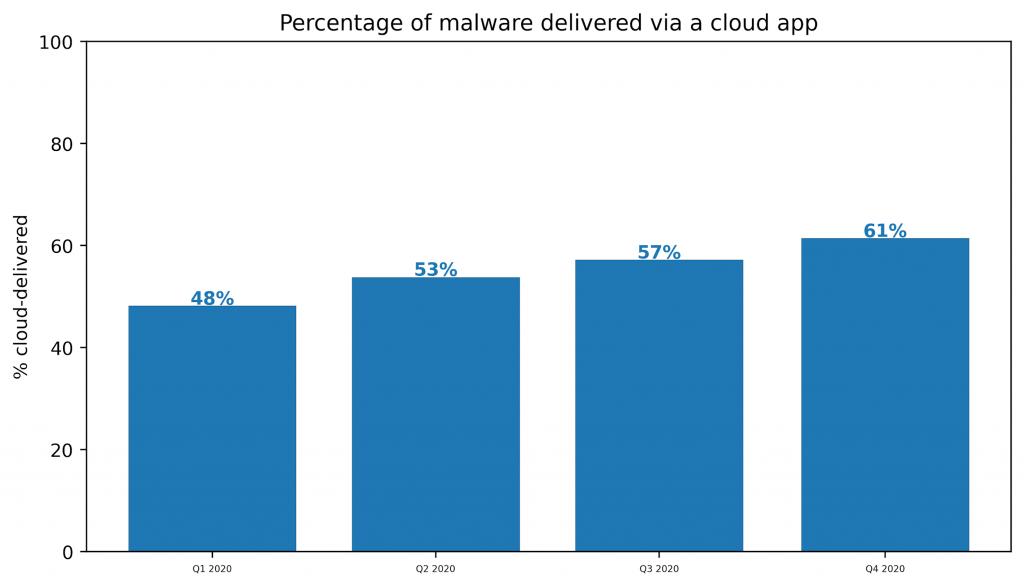
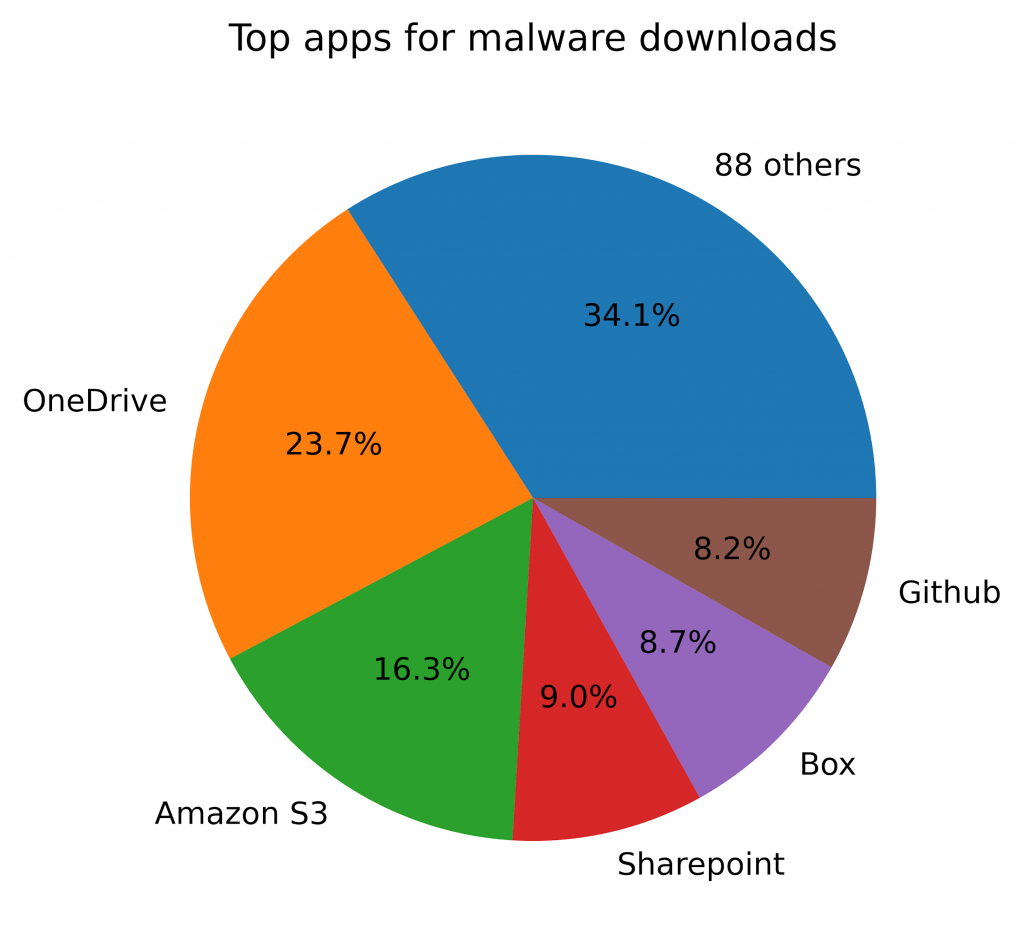
Over the same time period, the top five apps with which attackers had the most success accounted for more than 65% of the cloud-delivered malware. These top five apps—OneDrive, Amazon S3, Sharepoint, Box, and Github—are among the most popular apps used in the enterprise. Attackers have targeted these apps because of their popularity. Their attacks can abuse any trust placed in these apps and also blend in with normal activity.
Cloud Squirrel
CloudSquirrel is an infostealer malware campaign that abuses multiple cloud services to deliver both the initial Trojan and the next stage payload. For malware delivery, it abuses Amazon S3 and DropBox, which is number eight in terms of malware delivery, responsible for nearly 5% of malware delivery attempts in 2020.
CloudSquirrel likely originated in Brazil and typically arrives via an email phishing attack disguised as a tax document. After a series of cloud app redirects hosted on Jelastic and CloudApp, the victim downloads a malicious JAR file from Amazon S3. The JAR downloads additional malicious encrypted DES payloads from DropBox, which are later decrypted using the password “squirrel” — hence the name. The downloaded payloads exfiltrate email accounts and passwords to a traditional command and control server.
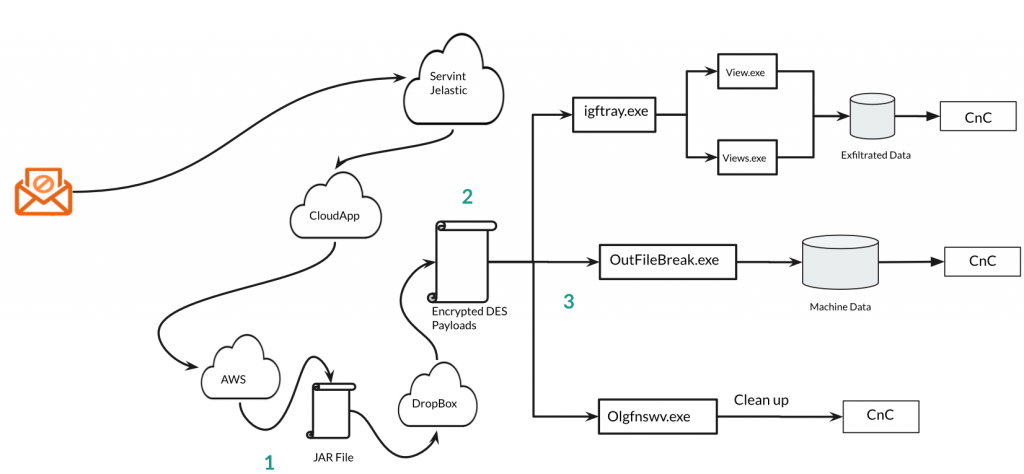
The following depiction shows:
- A JAR downloaded from AWS after multiple redirects from other cloud app platforms,
- The JAR downloading additional DES-encrypted payloads from DropBox
- Infostealers executing on the infected host, stealing data, and communicating with a command and control server.
Phishing
Cloud app credentials have long been a popular target of phishing credentials, with the Anti-Phishing Working Group (APWG) reporting that one-third of all phishing campaigns target cloud credentials. At the same time, 13% of all phishing lures in 2020 were themselves hosted in cloud apps. Cloud-hosted phishing is advantageous for attackers because their baits are hosted with cloud-provided domains and SSL certificates, adding legitimacy to their attacks. Cloud phishing elements are typically delivered in easy-to-deploy cloud templates. This means that if an attack element is blocked or taken down, the threat actor can easily move to another service or a new account within the same service.
Hackshit
Hackshit is a Phishing as a Service platform that allows its users to record the victims’ credentials using websockets over HTTPS or using decoy PDF documents with an embedded link. Their templates are designed to steal cloud credentials, including OneDrive, Google Drive, Dropbox, and DocuSign, and provided in a point and click interface shown below.

When the Hackshit phishing service was taken down, it quickly resurfaced, hosted by a different cloud provider. This is a common theme we have observed with cloud-based phishing campaigns. Whenever a bait is taken down, it is quickly replaced.
Command and Control
Over the past year, malware authors have used a variety of different apps for command and control, including cloud storage, chat, social media, and even video hosting. Like traditional command and control channels, cloud C2 channels have also frequently been abused for data exfiltration. Some of the apps that have been abused for command and control include:
- Amazon S3
- AWS EC2
- Azure AppService
- Azure Functions
- Azure Web Sites
- Discord
- DropBox
- Evernote
- Firebase
- Github
- Google AppEngine
- Google Drive
- Pastebin
- Slack
- YouTube
XBooster
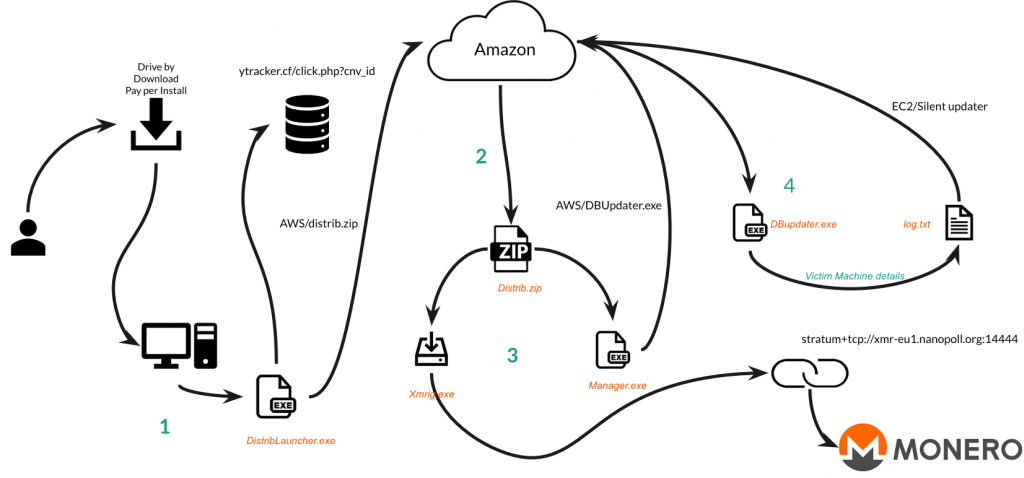
Xbooster is a parasitic Monero mining malware campaign that was successful in generating close to $100,000 USD using multiple Monero accounts. The campaign abuses Amazon S3 for malware delivery and abuses S3 and EC2 for command and control.
- The victim downloads and executes the first stage payload, DistrbLauncher.exe.
- This triggers a download of the second stage Distrib.zip from S3.
- The second stage launches Xmrig.exe to start mining and Manager.exe downloads yet another payload from S3.
- DBUpdater.exe communicates with a command and control server hosted in EC2.
Malware Propagation
Malware propagation occurs when an attacker uses a victim’s cloud app instance to try to spread throughout the victim’s network. Attackers leveraging cloud apps for malware propagation is still relatively rare. However, we expect this technique to grow in popularity along with remote work. In a distributed workforce, users might not share the same physical or virtual network, but they all collaborate using the same set of app instances.
Trickbot CRM Attack
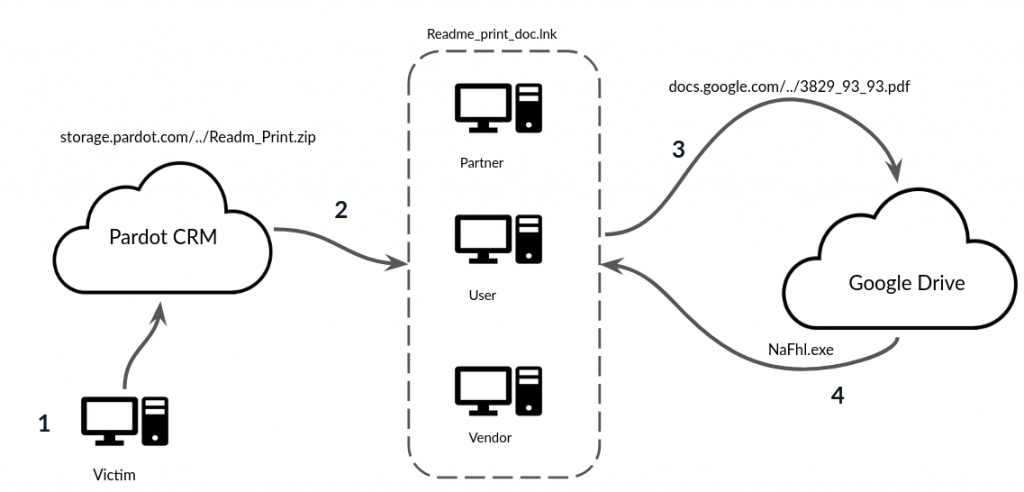
Trickbot is a banking Trojan that has been used in a variety of different malware campaigns. In one campaign, attackers compromised the initial victim’s Salesforce credentials and leveraged them to spread the Trickbot infection to secondary victims through Pardot.
- The attacker used the initial victim’s credentials to upload a Trojan to Pardot.
- The attacker shared the Trojan with the secondary victims, who were users with which the initial victim typically collaborates in Pardot.
- When the secondary victims opened the Trojan, it downloaded the Trickbot payload from Google Drive and infected their computers.
Data Analysis
The analysis presented in this blog post is based on anonymized usage data collected by the Netskope Security Cloud platform relating to a subset of Netskope customers with prior authorization.
Conclusions
Cybercriminals are actively abusing popular cloud services for malware delivery, phishing, command and control, and malware propagation. Our examples highlighted specific campaigns that abused popular cloud services to shine a light on the perils of trusting cloud services and highlight that cloud services should be approached with a zero-trust strategy. The malware propagation example underscores that even your organization’s own cloud app instances should not be trusted.
Comments are closed.