Michael Daniel is the President and CEO of the Cyber Threat Alliance (CTA), a US-based non-profit organization that enables cybersecurity providers to share threat information with one another in both automated and human-to-human fashion.
Introduction
The industry has talked about the concept of threat intelligence sharing for decades, yet it has struggled to adopt mechanisms that facilitate high-quality sharing at scale and that are sustainable, especially in the face of competitive pressures. This blog post surveys why these problems occur, how we might think about threat sharing differently in order to overcome them, and, ultimately, how threat intelligence sharing can improve the competitive edge of participating companies.
Typical arguments in favor of threat sharing — such as “it’s for the greater good” or “the bad guys do it, so the good guys should too” — may be true but are focused on altruistic considerations. Arguments for sharing rarely examine on how sharing might contribute to a company’s bottom line. CTA’s experience shows that threat intelligence sharing not only makes the entire industry better off but also directly improves the competitive edge of members.
What Makes Threat Intelligence Sharing So Hard?
In high-level terms, five issues can impede the effective sharing of threat intelligence:
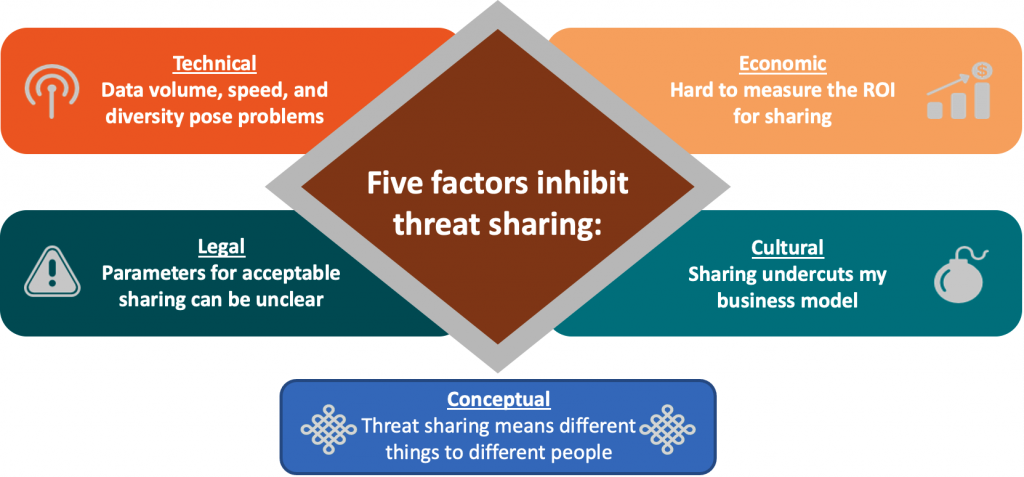
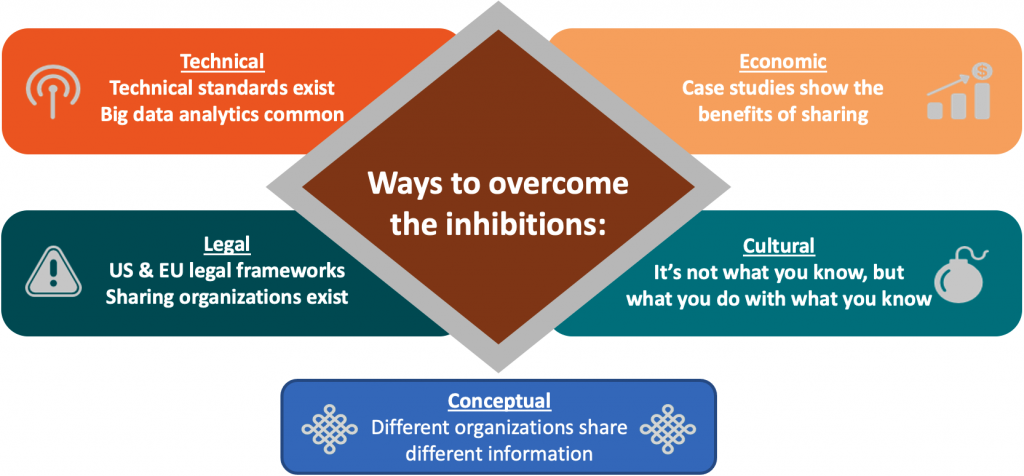
How Can We Overcome Barriers to Sharing?
Fortunately, over the last decade, we have developed tools to overcome these barriers:
Beyond Altruism: Why We Should Share Threat Intelligence
Although we have the means to overcome the barriers to sharing, sharing is not as widespread as it should be. Part of that gap is because proponents have not articulated clear arguments for sharing that go beyond altruism. Companies must have business-based reasons to share in order to spend the time and effort to engage in it. Based on our experience, we would argue that organizations should share threat intelligence for six reasons. Each of these reasons directly implicate a company’s competitive edge:
- No single company sees all malicious activity, so every organizations can learn something from sharing from the broader point of view that threat intelligence sharing provides.
- Regular sharing generates connections and ideas, while forcing organizations to defend their analytic conclusions in light of not only their data but the shared observations of peer institutions.
- Exchanging business cards in a crisis is a bad idea; threat intelligence sharing enables the development of connections ahead of time to make crisis response more effective in the moment.
- Cybersecurity is not a problem that can be solved without working together; no organization has expertise in all the facets of cybersecurity, so sharing is necessary in order to deal with the full spectrum of malicious activity.
- Increased security comes from acting on information; it’s not just what you know, but what you do with what you know that actually drives improved security.
- End-users are demanding a cross-cutting, industry-wide approach, hence having visibility into the actions and intelligence of peer organizations is key to identifying and leveraging your own comparative advantage.
Honing Your Threat Sharing Skills
Even if a company accepts these six reasons, sharing is still hard work. It takes resources away from other activities. Therefore, to get the most out of threat intelligence sharing and make it easier on your organization, you need to be asking and answering questions about sharing activities:
- What type(s) of information will be shared and in what form(s)?
- How can different parts of my company use the shared information?
- How will we measure the value of sharing over time?
- How will we integrate sharing into our regular business processes?
By asking these questions, organizations can position themselves better to define clear expectations up front and align sharing goals with business requirements. It is also important each organization considers the costs of sharing relative to its value to the entire organization — and works hard to improve the value proposition of the sharing arrangements over time.
Taking (Comparative) Advantage
Finally, once they have decided to engage in regular, sustained sharing, companies must decide what kinds of information to share and consume. Those decisions should be driven by the economic principle of comparative advantage. Since we are a sharing organization, CTA shares 10 different types of threat intelligence across 4 levels: technical (e.g., indicators), tactical (e.g., targeted warnings), operational (e.g., attribution), and strategic (e.g., best practices). However, most companies would likely only need a few of these information types.
Before entering into sharing arrangements, organizations should be clear on what kinds of information they are able to produce more effectively than their peers and what kinds of peer-produced information are most relevant to their business models. Different types of information have different intended audiences, enable different kinds of decision-making, and are useful across different timeframes:
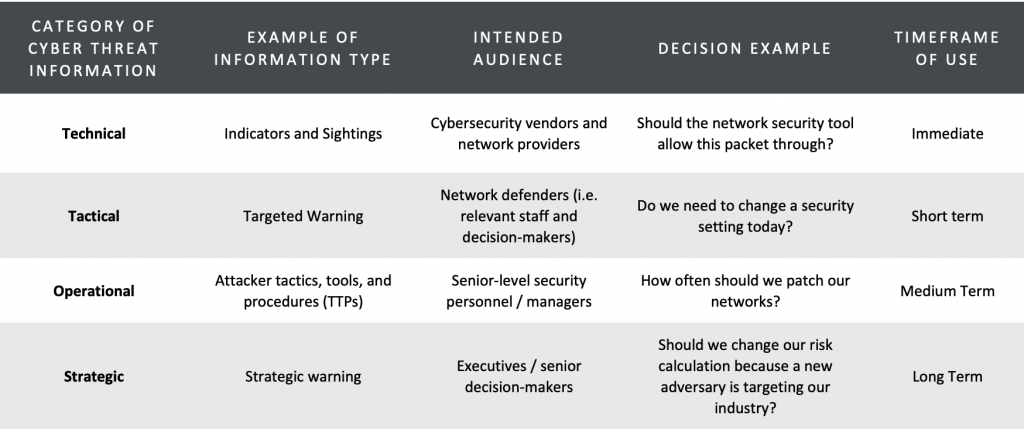
Making Sharing Work in Practice: Lessons Learned From CTA
Over CTA’s four years of enabling threat intelligence sharing across the cybersecurity industry, we have learned several lessons about how to make sharing work in practice:
- Something is better than nothing; you don’t have to share everything for sharing to be useful.
- Automated sharing is critical for technical data and is the only way to achieve scope and scale.
- Human-speed sharing is important too, since analytic work relies on more than just automated sharing.
- Early sharing fills in gaps and enhances defenses by enabling recipients to put in place protections ahead of public release.
- Campaign threat sharing amplifies actions; coordinated protections boost impact.
- Defensive measure threat sharing speeds up mitigation deployment, ensuring that customers can be protected more quickly.
- Situational threat sharing reduces the “fog of war,” in turn allowing the community to get to the right answer more quickly.
- Sharing is hard work. Technical elements are challenging, but non-technical elements (e.g., trust building) are even more difficult.
Conclusion
The cybersecurity community still has a great deal of work to do to make threat intelligence sharing operate with speed, scale, and regularity. We still need to identify specific actions for different parts of the ecosystem, identify and address further barriers to action, and work out how to collaborate more effectively to disrupt adversaries on a systemic basis. In addition, law and policy needs to continue evolving to support sharing and collaboration activities.
However, we already know that sharing makes companies more competitive. The bottom line is that a company’s competitive edge comes primarily from its analysis and action, not the availability of raw data. At the same time, the precise ways in which sharing advances a company’s business interests will be highly varied, depending on the company’s business model. As such, while threat sharing is hard work and requires ongoing investment, it is an essential component of our efforts to improve security across the digital ecosystem. The more organizations that do the necessary work to figure out where they can best fit into that sharing picture, the better off we’ll be.
Does your organization have threat intelligence to share? Contact us today to learn more about CTA membership!
Comments are closed.





