Being one of the most popular computing platforms ever, Android has essentially become a sweet spot for cyber criminals. In the contemporary digital fraternity, where security has become almost a myth, the service and platform providers as well as the users need to expend continuous efforts to keep data secure from prying eyes.
However, the adversaries also expend similar (if not more) efforts to identify and/or track vulnerabilities, 0-days and otherwise, to exploit.
The Rise
Let’s take Cerberus for example, one of the prevalent Android Trojans as of few months ago. Offered as Malware-as-a-Service (MaaS) and advertised using flashy banners on the dark web to captivate significant number of buyers, Cerberus has been available on a subscription basis at almost “compelling” rates. An evil minded individual could avail the service at a discounted price and enjoy constant support from the social-media friendly developer.
Cerberus, a sophisticated Android Trojan with self-propagating abilities mostly used for eliciting banking and financial credentials, gets installed on the victim’s device via numerous campaigns.
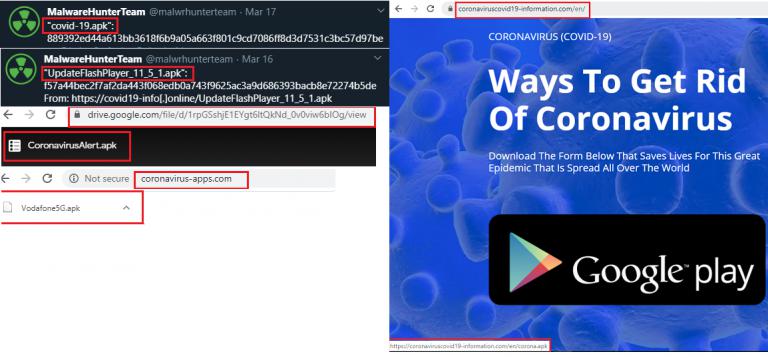
Researchers at K7 Labs spotted a minacious strain of this Android Trojan in the wild masquerading as a COVID-19 tracker app. And their investigations revealed several interesting facts about this variant of the malware, especially from an Indian context. Earlier strains of Cerberus were targeting over 250 banking and cryptocurrency applications from the United States, France, Italy, Turkey, and Japan.
This variant was however found to be targeting several large Indian banking institutions (including Axis Bank, ICICI Bank, Indian Bank, ING Bank, HDFC Bank, and Bank of Baroda) by way of not-so-ingenious techniques.
The Reign
Once installed on the target device, the malware uses the Flash Player icon as its own for the first launch, after which it goes into stealth mode by hiding its icon from the application drawer.
Soon after installation, it continually brings up the accessibility settings option on the device until the user enables it. For the uninitiated, apps having the accessibility settings turned on could carry out numerous functions in the background that could be used to track the user’s activities.
Interestingly, it also tries to evade the Google Play Protect constant scan by disabling the “Google Play Protect” service.
Thus comfortably settled in, the malicious app monitors the device to see if any of the targeted applications are being launched.
And when that happens, it launches a screen overlay attack: it opens up a fake login screen, a look-alike of the actual app the user intended to open, prompting the unsuspecting user to enter their credentials.
This variant comes with a key-logger functionality that can record keystrokes and sounds. So when the user types in their financial credentials, it tracks every key tapped and sounds, and saves them into a log file called keys.log.
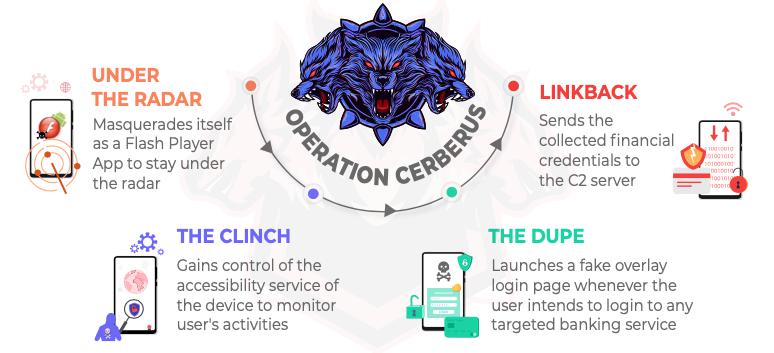
Moreover, it lists all the installed packages on the infected device and forwards the list, along with all the other stolen information, back to its C2 (Command-and-Control) server(s).
In addition to the above tasks, the malware is also capable of the following malicious activities:
- Collecting device information
- Downloading additional payloads
- Removing other installed apps
- Stealing contact lists
- Sending, receiving and deleting SMS
- Taking screenshots
- Forwarding calls
- Locking device display
Our researchers also found that this piece of malicious code comes with Remote Access Trojan (RAT) functionality from a RAT Service, and it awaits a hardcoded list of commands from its C2 server(s). The command list includes:
- opendir
- startscreenVNC
- stopscreenVNC
- downloadfile
- startsound
More recent variants of the malware have aimed to exfiltrate credit card data stored on the device and have been noticed to use SQLite database for storing the stolen information.
Also, to evade detection all the strings in this variant were base64 encoded and the resulting decoded strings are RC4 encrypted strings with a decryption key specific to each string. Interestingly, each encrypted string has its unique RC4 decryption key prepended as the first 6 bytes of the encrypted string.
The Fall
Fortunately, the mayhem of Cerberus is expected to be short-lived thanks to a purported breaking up of the team which resulted in their inability to “support their product”, and its developer(s) have since reportedly put their wares, so to speak (source code, admin panel, servers, active customer lists, etc.), on auction for USD 50,000 or a final deal price of USD 100,000.
Of course, the postlude doesn’t necessarily mean their evil aura is gone forever. Cerberus’s ending might be a new beginning for another, maybe a more severe malware, as the future buyer(s) could make a comeback, or worse add more sinister features to it to create havoc in the coming months.
So in conclusion, these attacks are going to keep coming in different avatars, each new one probably more sophisticated (or in the very least more unscrupulous) than the ones before. And here are some tips to best protect your device and data:
- Install a robust security product for Android, like K7 Mobile Security, and ensure it is kept up-to-date
- Keep your devices updated and patched for the latest security vulnerabilities
- Be vigilant about what you download, and where you download them from; exercise caution even while installing apps from the official App Store
- Disable “Install unknown apps” option on your Android device, never download apps from 3rd party app stores
- Check app permissions during installation and abort if unnecessary privileges are requested
- Do not click on links in SMS and emails, especially if you do not know the sender
Comments are closed.





